Security researcher Mathy Vanhoef discovered several security vulnerabilities that affect most Wi-Fi devices. The collection of attacks, called FragAttacks, which stands for fragmentation and aggregation attacks, requires that that attacker is within range of the wireless network.
Three of the discovered vulnerabilities are “design flaws in the Wi-Fi standard” according to Vanhoef, and therefore affecting most Wi-Fi devices. Additional vulnerabilities were discovered during the research that were made possible by “widespread programming mistakes in Wi-Fi products”.
The vulnerabilities affect all security protocols of the Wi-Fi standard, including the latest WPA3 specification but also WPA2 and WPE.
The researcher notes that the programming mistakes are the biggest concern because of their exploitability. The vulnerability was disclosed to the Wi-Fi Alliance and ICASI, and manufacturers of Wi-Fi devices had nine month time to create security updates for their devices to protect customers from potential attacks.
Devices should be updated if manufacturers have released updates that address the issues. Some issues can be mitigated using HTTPS.
Vanhoef published a video on YouTube in which he demonstrates attacks that exploit the Wi-Fi implementation flaws.
The following vulnerabilities have been disclosed:
Plaintext injection vulnerabilities
An attacker can construct unencrypted Wi-Fi frames that are accepted by target Wi-fi devices. Some wireless devices accept these frames automatically, others may accept plaintext aggregated frames if they “look like handshake messages”
This can for instance be abused to intercept a client’s traffic by tricking the client into using a malicious DNS server as shown in the demo (the intercepted traffic may have another layer of protection though). Against routers this can also be abused to bypass the NAT/firewall, allowing the adversary to subsequently attack devices in the local Wi-Fi network (e.g. attacking an outdated Windows 7 machine as shown in the demo).
Design flaw: aggregation attack
The “is aggregated” flag is not authenticated, which means that it can be modified by attackers.
An adversary can abuse this to inject arbitrary network packets by tricking the victim into connecting to their server and then setting the “is aggregated” flag of carefully selected packets. Practically all tested devices were vulnerable to this attack. The ability to inject packets can in turn be abused to intercept a victim’s traffic by making it use a malicious DNS server (see the demo).
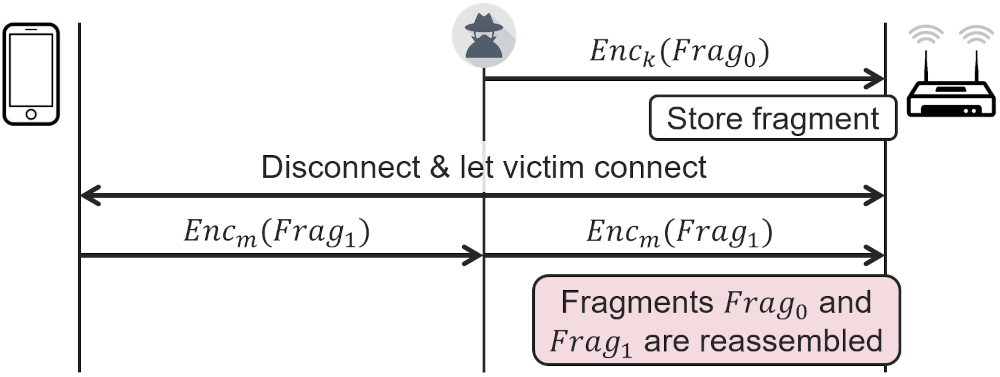
Design flaw: mixed key attack
Frame Fragmentation was designed to improve the reliability of Wifi connections by splitting large frames into smaller ones. Problem is, that receivers are not required to check if the fragments have been encrypted using the same key, and that means that fragments that were decrypted using different keys may be reassembled.
This design flaw can be fixed in a backwards-compatible manner by only reassembling fragments that were decrypted using the same key. Because the attack is only possible under rare conditions it is considered a theoretical attack.
Design flaw: fragment cache attack
Another flaw in Wi-Fi’s frame fragmentation feature. Wi-Fi devices are not required to remove non-reassembled fragments from memory when a client disconnects. The attack injects a malicious fragment in the memory of the access point so that the injected fragment of the attacker and the fragmented frame of the client will be reassembled on reconnect.
If the victim sends fragmented frames, which appears uncommon in practice, this can be abused to exfiltrate data.
Here is the full list of CVE identifiers:
- CVE-2020-24588: aggregation attack (accepting non-SPP A-MSDU frames).
- CVE-2020-24587: mixed key attack (reassembling fragments encrypted under different keys).
- CVE-2020-24586: fragment cache attack (not clearing fragments from memory when (re)connecting to a network).
- CVE-2020-26145: Accepting plaintext broadcast fragments as full frames (in an encrypted network).
- CVE-2020-26144: Accepting plaintext A-MSDU frames that start with an RFC1042 header with EtherType EAPOL (in an encrypted network).
- CVE-2020-26140: Accepting plaintext data frames in a protected network.
- CVE-2020-26143: Accepting fragmented plaintext data frames in a protected network.
- CVE-2020-26139: Forwarding EAPOL frames even though the sender is not yet authenticated (should only affect APs).
- CVE-2020-26146: Reassembling encrypted fragments with non-consecutive packet numbers.
- CVE-2020-26147: Reassembling mixed encrypted/plaintext fragments.
- CVE-2020-26142: Processing fragmented frames as full frames.
- CVE-2020-26141: Not verifying the TKIP MIC of fragmented frames.
A research paper is available with additional details.
The post FragAttacks: vulnerabilities that affect Wi-Fi devices appeared first on gHacks Technology News.
