Microsoft has integrated the driver userChoice Protection Driver, short UCPD, into Windows 10 and Windows 11 systems recently. This driver has just one purpose: to block access to UserChoice Registry keys.
These Registry keys define the default programs on the system. There are keys for the default web browser, PDF Viewer, or image editor. Keys exist for file extensions and protocols as well.
Microsoft introduced a new convoluted way of changing default apps and file extension associations in Windows 11 for users. You can check out our guide on setting default apps on Windows 11 here.
Up until recently, programs could make changes to the UserChoice Registry keys to change default parameters. A web browser could set itself as the default program for all supported file types. Provided that the user wanted this, it make things a lot easier thanks to the automated way of changing defaults.
Specialized programs, such as SetUserFTA or Sophia Script, included the functionality as well. They made it easier for home users and administrators to change defaults on Windows machines.
Find out if UCPD is installed
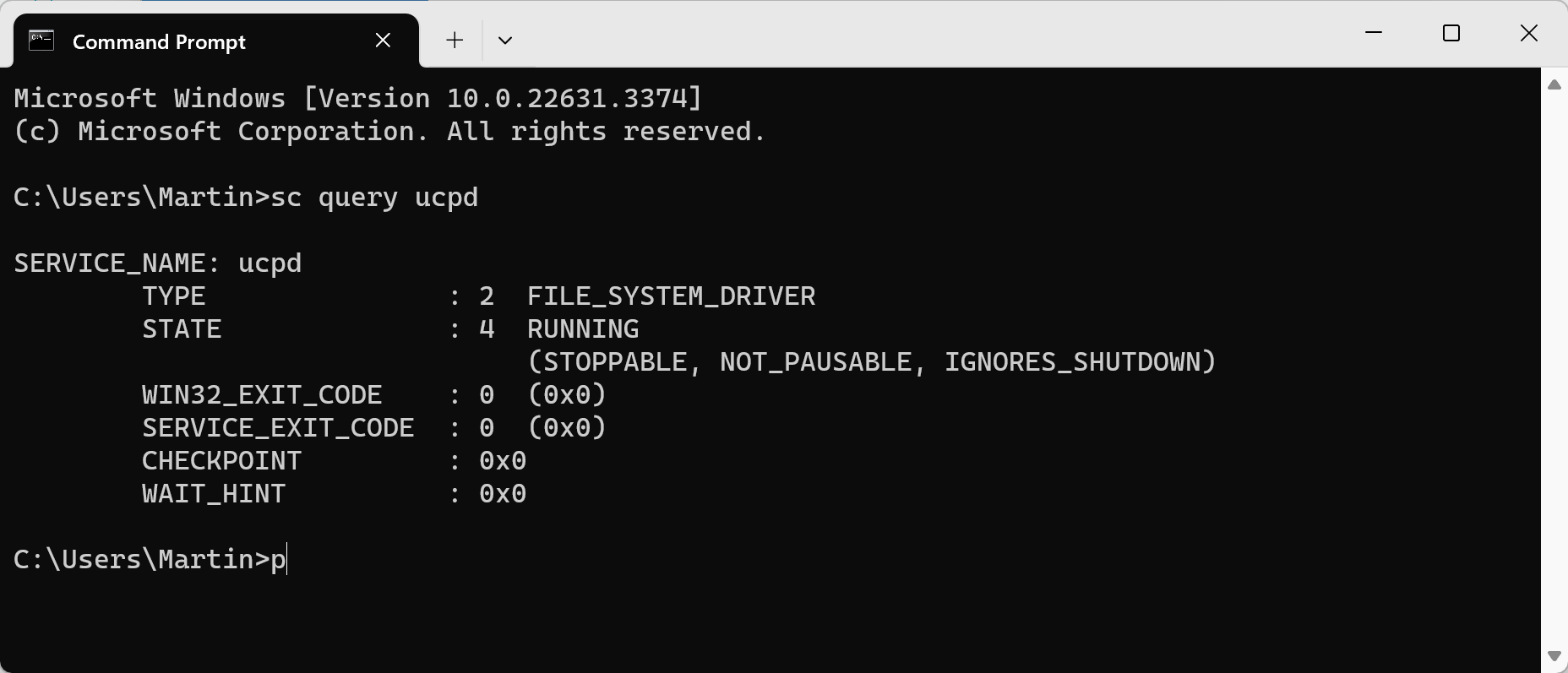
You are probably wondering if the filter driver is installed and running on your Windows system. Here is how you can determine that:
- Open Start, type cmd and select Command Prompt from the results.
- Type sc query UCPD.
How UCPD works
Gunnar Haslinger published an analysis on his blog. The filter driver blocks access to certain UserChoice Registry keys by returning access denied.
Microsoft still allows access, but only for processes that pass the following verification:
- Is the process signed by Microsoft?
- Is the process on the deny list?
In other words: any third-party program that tries to make changes to default apps, file extension handline or protocols on Windows is blocked from doing so.
The deny list includes Windows tools, likely to prevent third-party developers from using them as a workaround. Tools like regedit.exe, reg.exe, or powershell.exe are on the deny list.
Can you stop UCPD?
It takes two steps to put an end to UCPD.
- Set the startup type of UserChoice Protection Driver to disabled.
- Deactivate the UCPD Velocity task in the Task Scheduler.
Step 1: Change the startup type of UCPD to disabled
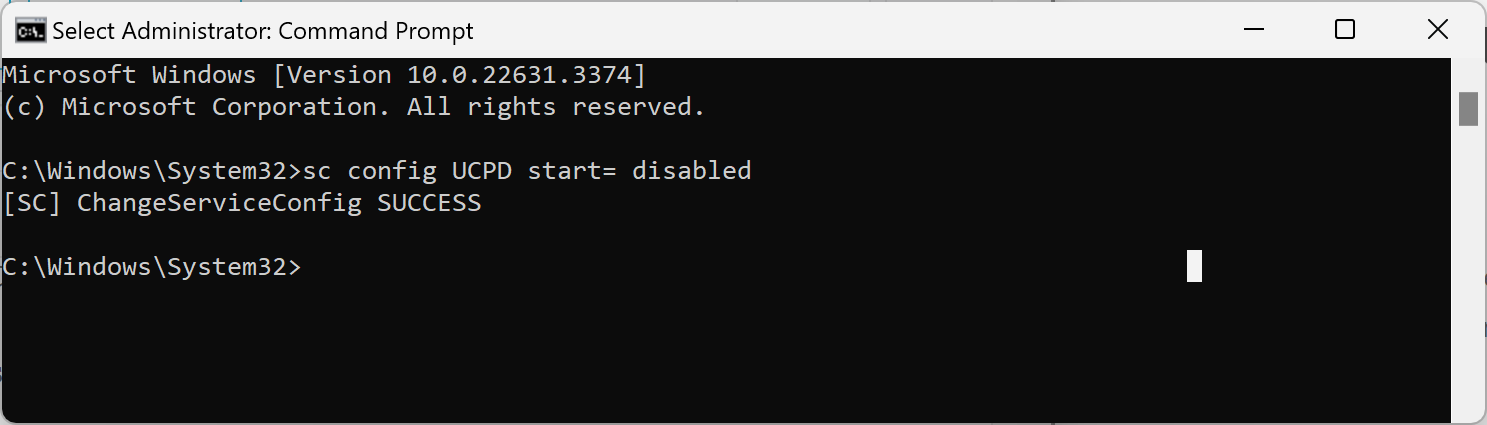
It is necessary to block the filter driver from starting with Windows. Here is how that is done:
- Open Start, type cmd, and select run as administrator.
- Execute the following command: sc config UCPD start= disabled
Step 2: Deactivate UCPD Velocity in the Task Scheduler
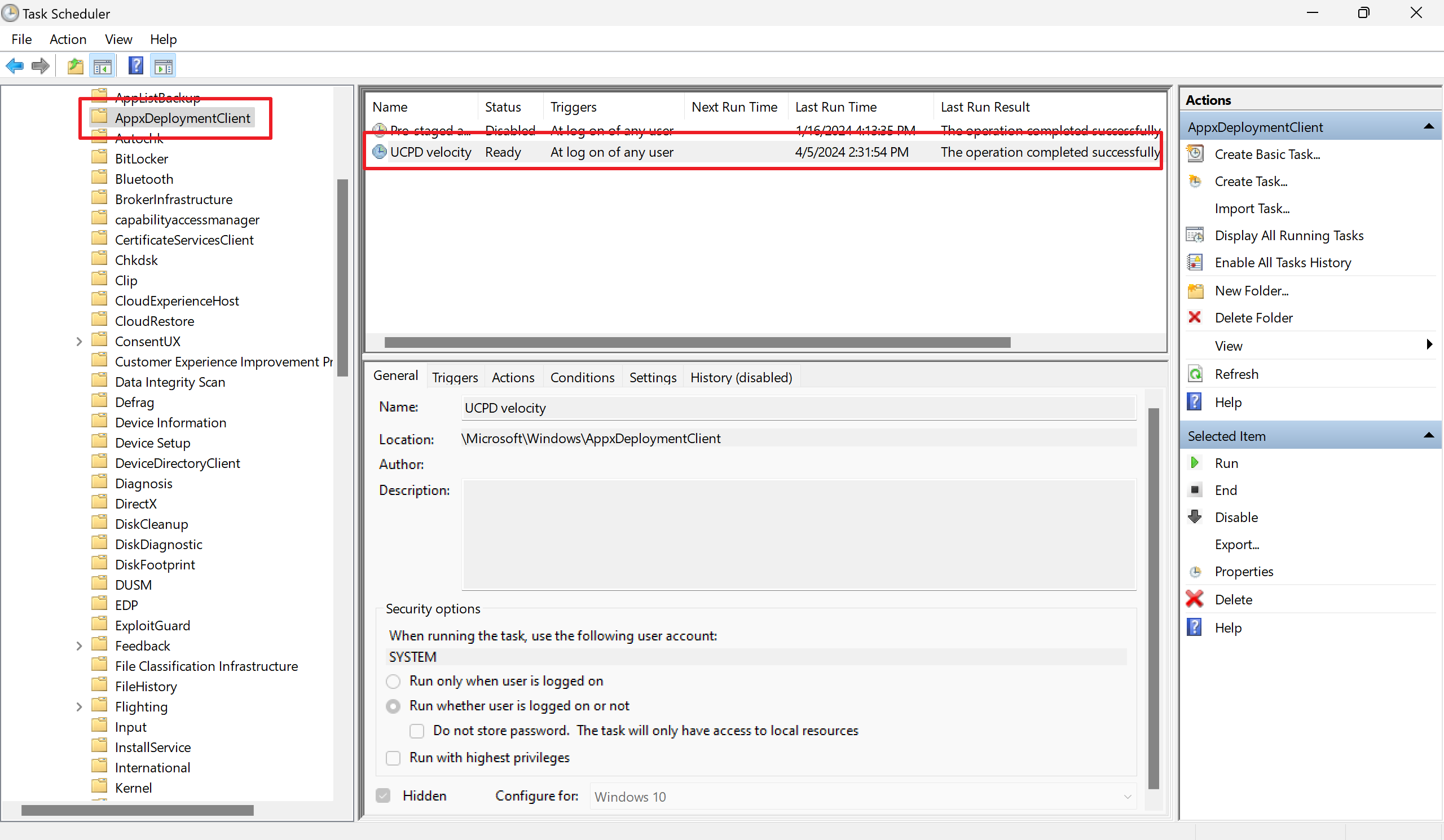
The UCPD Velocity task has a single purpose: make sure that the filter driver runs. It does so after each user sign. If its validation fails, it will reset the startup type of the UCD service to system start to make sure that it starts with the system. It will furthermore start the service to make sure the filter runs on the device.
While starting is possible at any time, disabling is not. Disabling works only if the startup type is set to disabled and the system is restarted.
The task checks the value of FeatureV2 in HKLMSYSTEMCurrentControlSetServicesUCPD as well. If not set to the value 2, it will set the value to it.
Here is how you disable the task:
- Open Start.
- Type Task Scheduler.
- Select “Run as administrator” from the list of options.
- Use the sidebar to go to Task Scheduler Library > Microsoft > AppxDeploymentClient.
- Right-click on the task and select “disable”.
You may also run this from an elevated command prompt: schtasks.exe /change /Disable /TN “MicrosoftWindowsAppxDeploymentClientUCPD velocity”
A restart of the system is required to complete the process.
Closing Words
Microsoft did not announced the new filter driver on any of its sites or blogs to the best of my knowledge. It is therefore unclear why it was introduced.
When you look at the filters functionality, you will notice that it blocks third-party programs from making changes to the defaults. Microsoft’s filter makes no distinction here; legitimate programs such as web browsers are blocked, even if the user wants the changes to the defaults to be made.
Similarly, specialized programs, such as the aforementioned SetUserFTA are also blocked. These are usually run by users and administrators to make “wanted” changes to the system.
Clearly, Microsoft is reducing user choice and abilities with the new filter driver. Even if it is designed to protect against certain types of malicious software, it has the side effect of removing options from users. It is also clear that Microsoft is the benefactor here, as it is now more difficult to change defaults on Windows machines.
There will be workarounds and likely a cat and mouse game between Microsoft adding workarounds to the deny list and developers finding new ways to make the changes.
The post New sneaky Windows driver UCPD stops non-Microsoft software from setting defaults appeared first on gHacks Technology News.
